Reports
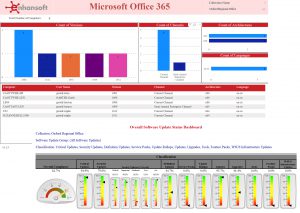
Sample results for all Enhansoft Reporting dashboard and reports for both Power BI and SSRS.
-
Configuration Manager (42 Articles)
-
Endpoints (74 Articles)
-
Security (47 Articles)
-
Software (62 Articles)
-
Users (11 Articles)